Owning and running a small business can be a lot of work, so IT security often falls on the back burner – understandably so. When you’re split between providing customers excellent service and making your business thrive, it’s easy to forget about the lurking threats in the invisible IT world.
Take it from us – Protek-IT has been working on securing and protecting small businesses for years. We know the most vulnerable points in many small companies and the easy, inexpensive solutions to fix them.
(according to Verizon’s Data Breach Investigations Report in 2020, 28% of breaches affected small business employees)
So many small businesses get targeted by hackers or scammers because they usually don’t have a lot of safety precautions in place. Their data is still valuable, but unlike big companies – there are no guards.
These little tips will not cost you a fortune and mainly require a little forethought. Similarly to insurance policies, they will give you peace of mind and save you money and time in the long run.
Email hygiene
- Many scammers use emails as the first point of entry as it takes the least amount of time, and they can send hundreds or thousands of emails to different companies and only focus on the ones that reply.
To be hygienic with your emails, you should:
- Always double-check the sender email
For example, scammers often create a similar email to a standard service provider – like su************@***********lp.com instead of the original su*****@*******ft.com. When in doubt, Google the sender and the subject line – you will often see others asking the same questions. - Check links before opening them
Most email providers show you where the link is directing you before you click on it. All you need to do is hover over the link and see if it looks legitimate. If the link is labeled as Microsoft 365, but the link takes you to some garbled string of letters and numbers – don’t click on it. - Watch out for typos
Have you ever wondered why so many scam emails are riddled with typos? It’s to catch people who don’t pay much attention or are in a hurry. Those two traits make it more likely for them to go through with the actual scam part – such as sending money, buying something online, sharing their CC number, etc. Watch out for some apparent typos – like the company name, the signature, or greeting being misspelled. - Use email security services, if possible
This type of software automatically blocks malicious senders, so you don’t need to go all Sherlock Holmes on every email that comes in your mailbox. It can help you save time and provide another layer of security. Reach out to our IT Services techs for more info.
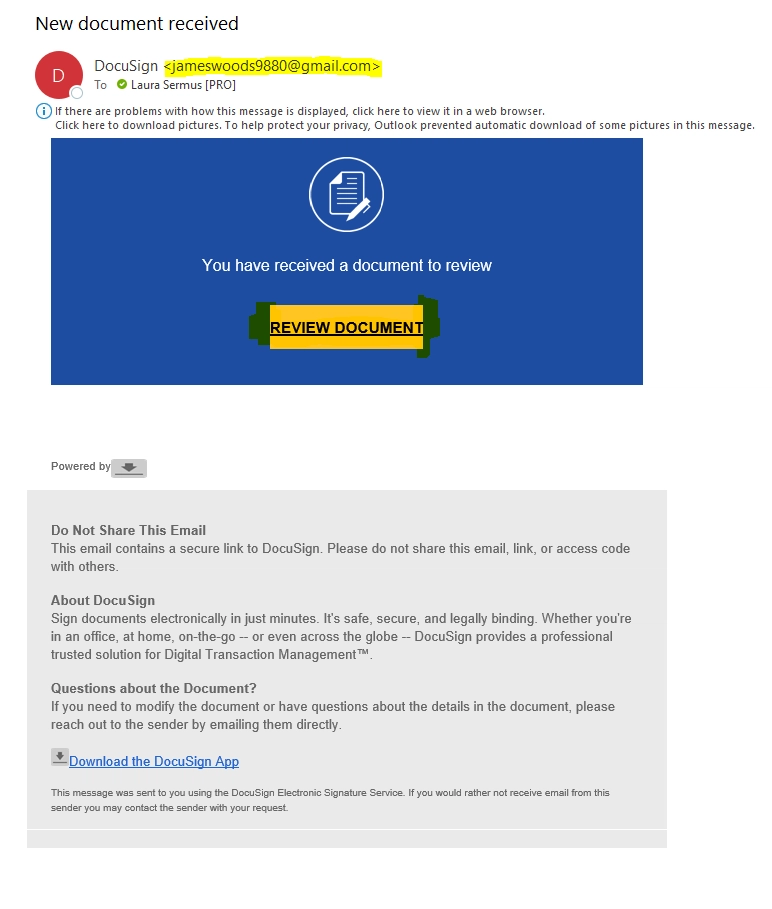
This is an example of a scam email I received. It’s done pretty well as you won’t find any glaring typos.
The giveaways for this one are:
- It’s coming from an unknown sender. I have never heard of that person.
- There is no spacing around the sides of the yellow button – such a small thing can mean it’s not legitimate.
- It doesn’t have any real info in the email – I need to click on the button to see anything at all.
- When I hover over the links, it doesn’t direct me to the DocuSign page.
To see a legitimate DocuSign email and compare these two, visit the DocuSign website.
Enforce safe password policies / multi-factor authentication
As easy as it sounds, complex and unique passwords can improve your security by a lot. It’s not as easy to remember them – we know.
- Follow the standard password-creation rules:
use a number, a mix of capitals and lowercase characters, one unique character, and no common words. - Do not reuse passwords
Easier said than done. But this is especially dangerous in a business environment – you might reuse the password for something you don’t think that matters – like an old social media account or a news subscription for something more substantial, like a bank account.
When one non-important website leaks, it’s not hard to use your email/username with the password for all the essential stuff. The good news? A password manager works great for remembering your unique passwords and making them essentially non-hackable (scroll to the bottom to ask us more!)
- Use 2FA (2 Factor Authentication) whenever possible
2FA requires you to confirm your identity with two different accounts – after typing in the correct password; you will receive a confirmation code on your email or via text.
The chances someone else has access to several of your accounts are pretty slim. Again, this can be a pain – but password managers also take care of this by automatically creating a code and filling it out. We can help you get set up with Password Managers or setting up 2FA.
Train all employees
Every employee who has any access to any company files should be made aware of possible threats. Their training should include letting them know of all the potential risks in the first point, plus:
- If employees use their devices for company emails or other files, ask them to keep everything updated
Of course, your company-owned computers (or BYOD devices) should always be up-to-date as well. - Inform employees about phishing emails
where the scammer is trying to impersonate someone else to get information. Watch out for typos-links-senders! - Warn them about social engineering,
which means scammers are manipulating users into giving them info voluntarily. It might take the form of a new internet “friend” who really wants to get to know you (and fast!), especially your pet’s names, your first car model, and your childhood home’s street name.
Or it might be someone pretending to be an old acquaintance in need of help.
Keep your data backed up
You have probably dealt with a situation where you created a file, edited it, and spent a ton of time on it, only to have your computer crash or shut down – resulting in a complete loss of data.
Now imagine that happening to your company files, user accounts, invoices, blueprints, etc. Yikes.
- Create a backup,
whether stored in the Cloud (safer/automatic/recurring cost) or on a physical device like an external hard drive (prone to failing/more manual/one-time cost). Not much better than getting back hours of work you thought was gone forever. - Make sure to back up regularly, and keep several backups
Remember – one is none, and two is one. Ideally, your files have several copies saved automatically in case you accidentally overwrite something you didn’t mean to.
Use the principle of least privilege
This principle means employees should have the minimum permissions to start. For example, only allow them to view shared files or allow access to only their personal email.
Then, when they get more responsibilities, you can increase the privilege of editing files and gaining access to shared mailboxes. Issues caused by too many privileges are usually not malicious, but just accidental.
Use a VPN or Virtual Desktop if not at the office
A VPN creates a safe, private, and encrypted tunnel from wherever you are to the office. Getting access to your business files is much safer to do via a Virtual Private Network.
Make sure all employees who work from home or often travel have access to VPN.
You can set up a simple desktop icon they can click to use the network in the office from on the go – convenient for them, safe for you.
A more modern option is to use Azure Virtual Desktop, which stores your entire desktop, including all the files you might need and use, in the Cloud. Access from any device, anywhere.
Secure your website
If your site has an option to fill out forms or if you sell anything online, it’s essential to keep it safe.
- Protect your website with an SSL encryption certificate
You can see if your site has a certificate by typing in your website name to your browser and seeing if there is a padlock on the left side of the URL.
This padlock indicates that all data coming from and going to the website will be encrypted and can’t be intercepted. You can usually purchase an SSL cert from your website hosting provider.
- Keep your website platform up-to-date
Most modern website platforms (WordPress, Weebly, Google Sites, etc.) require updates to patch potential security holes.
You can also run useful site health checks to tell you if anything is critically wrong. You could use THIS website to check errors on your website – using the free version usually gives you a good idea of the significant issues.
Destroy physical data
Just invest in a good shredder, and you’re good. If you plan on recycling your old computer, make sure the hard drive is empty. If needed, just take a good ol’ hammer to the hard drive.
If keeping an eye on all the tips mentioned above proves too time-consuming, you might want to get some help. Protek-IT offers reliable skilled Managed IT Services for small businesses.
That way, you can sit back and watch your company become more secure as your employees get more knowledgeable.



