Tech Blog
Looking for troubleshooting tips and articles? See here.

Is Your Office Quietly Leaking Data?
As August rolls in and summer starts to wind down, it’s the perfect time to get back into a steady routine. That includes refreshing the habits that keep your digital
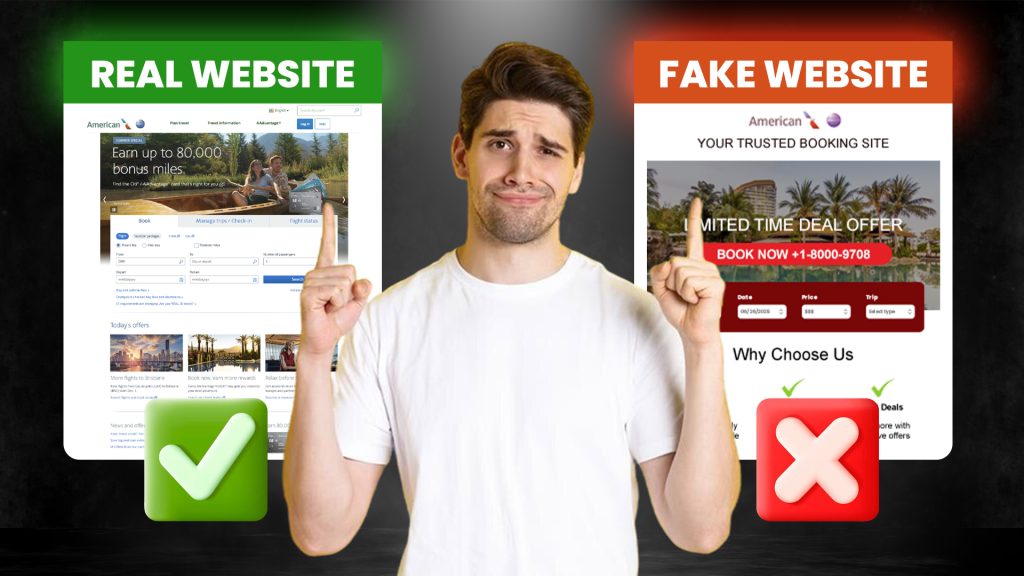
The One Click That Could Ruin Your Vacation
Just because summer is winding down doesn’t mean travel scams are slowing. Late-season trips, including Labor Day getaways, are prime time for cybercriminals to target distracted travelers. Falling for one

Heatwave Tech Tips: Preventing Overheating and Extending Device Lifespan
Sunny weather is great for barbecues and beach days, but not for your electronics. Heat can quietly wear down your devices, especially if you’re working outside or bringing tech along

How AI Is Supercharging Cyber Threats This Summer
Summer often brings a spike in online scams. This year, artificial intelligence is helping cybercriminals create fake travel deals, booking confirmations, and giveaways that look more believable than ever. Scams

Is Your Data Safe? Backup and Recovery Tips for a Safer Summer
Summer’s a great time to unplug, travel, and take a break… but it’s also when devices tend to get lost, damaged, or hit with unexpected issues. Between water damage, dropped

Summer Cybersecurity: Keeping Kids Safe Online During Break
When school’s out, screens tend to take over. With more free time during the day, kids often spend it gaming, watching videos, or scrolling through social media. That extra time

Graduation Season: Protecting Young Adults from Cyber Threats
The diploma isn’t even framed yet, but hackers are already rolling out the welcome mat. The moment graduates start job hunting, their personal data becomes prime real estate for cybercriminals.

National Password Day: Are Your Passwords Strong Enough?
Every year, the list of the most common passwords circulates on the internet, and every year, it’s just as concerning. People are still using “123456” and “password” like it’s 1999.

10 AI Tools to Simplify Your Office Workflow
Artificial intelligence tools are becoming everyday essentials in the workplace. These tools don’t just save time—they also make tasks more manageable and efficient. Here’s a breakdown of AI tools that

The Role of Dark Web Monitoring
The internet you use every day—the websites you visit, the emails you send, the apps you rely on—is just the surface of a much larger network. Below that lies the

Top Windows 11 Settings for a Smarter, Faster Workflow
As of October 2024, Windows 11 has surged to over 35% of the Windows market share, reflecting its growing adoption among users. With Windows 10 support ending in October 2025, now

Strengthen Your Email in 6 Steps
Ever wonder how many times your email has been targeted by cybercriminals this week? While you’re reading this, hackers could be probing your inbox for a way in. It’s no

Essential Settings to Maximize Your Microsoft 365 Experience
Microsoft 365 is packed with tools that help businesses get more done and work better together. But many people and small businesses aren’t using it to its full potential. There

The Real Costs of IT Downtime
It’s Monday morning, and you walk into your office, ready to get things done. But something’s wrong—your computers are frozen, phones aren’t working, and the internet is down. Everything grinds

How to Use Technology to Get More Done at Work
Gone are the days of cluttered desks and bulky filing cabinets. Today’s offices are all about efficiency, with technology making things easier. The right tech tools can boost your team’s
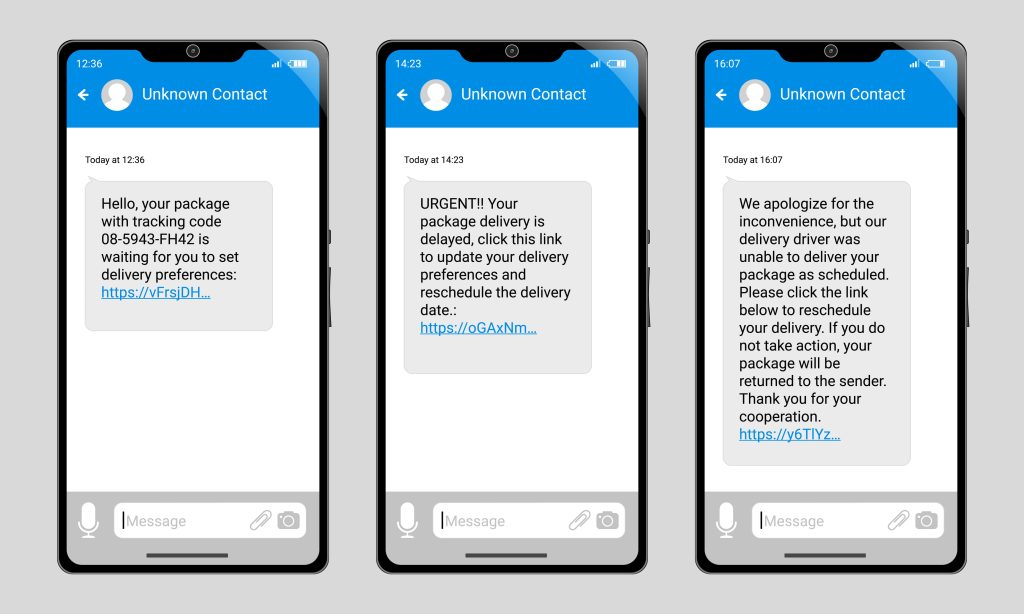
AI-Driven Phishing – Understanding and Preventing Attacks
Phishing has always been a threat, but now, with the rise of AI, it’s even more dangerous — phishing 2.0 is here. It’s smarter, more convincing, and harder to detect.

